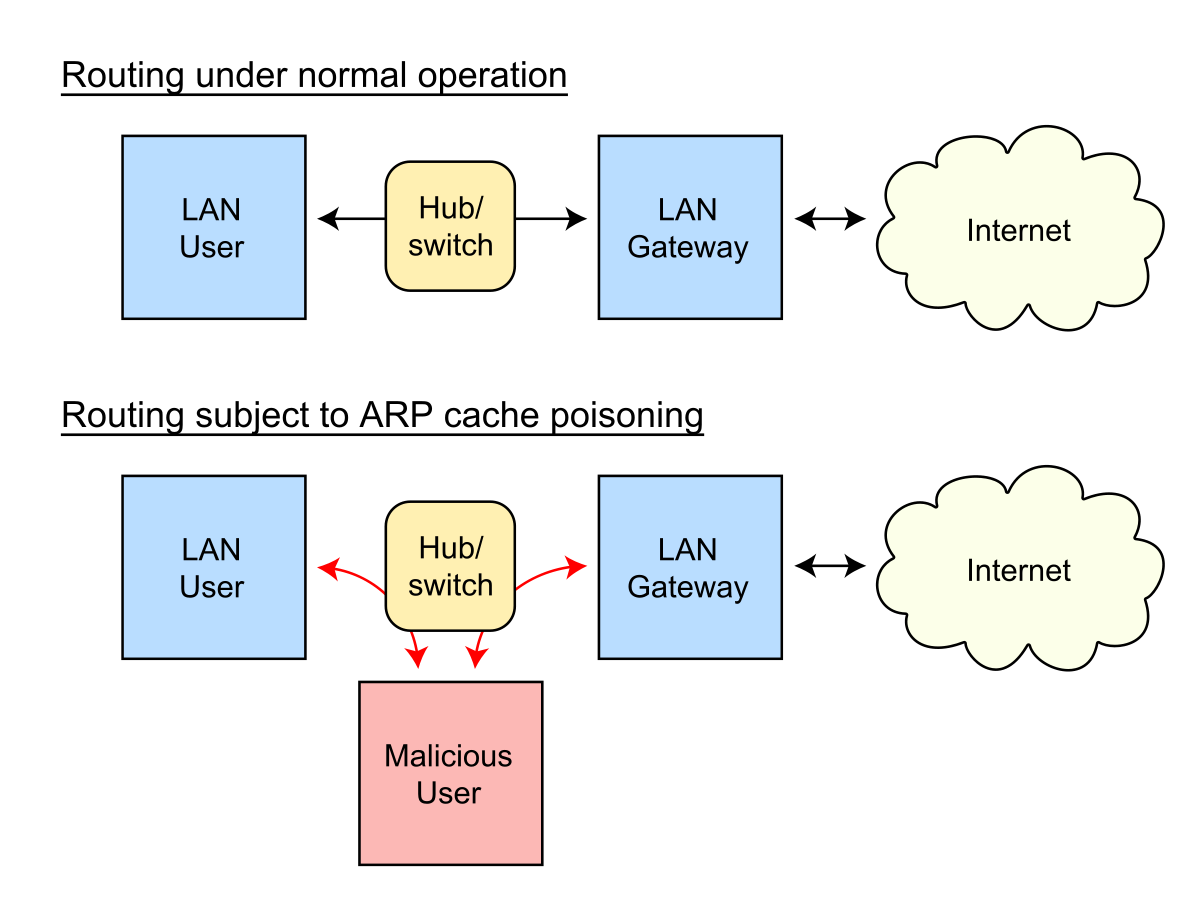
When an Internet Protocol IP datagram is sent from one host to another in a local area network , the destination IP address must be resolved to a MAC address for transmission via the data link layer. Generally, the goal of the attack is to associate the attacker's host MAC address with the IP address of a target host , so that any traffic meant for the target host will be sent to the attacker's host. Well, that will be the router that the Virtual Machines are connected to. Hence the network flows through the hacker. OpenBSD watches passively for hosts impersonating the local host and notifies in case of any attempt to overwrite a permanent entry [8]. How To Install Kali Linux? 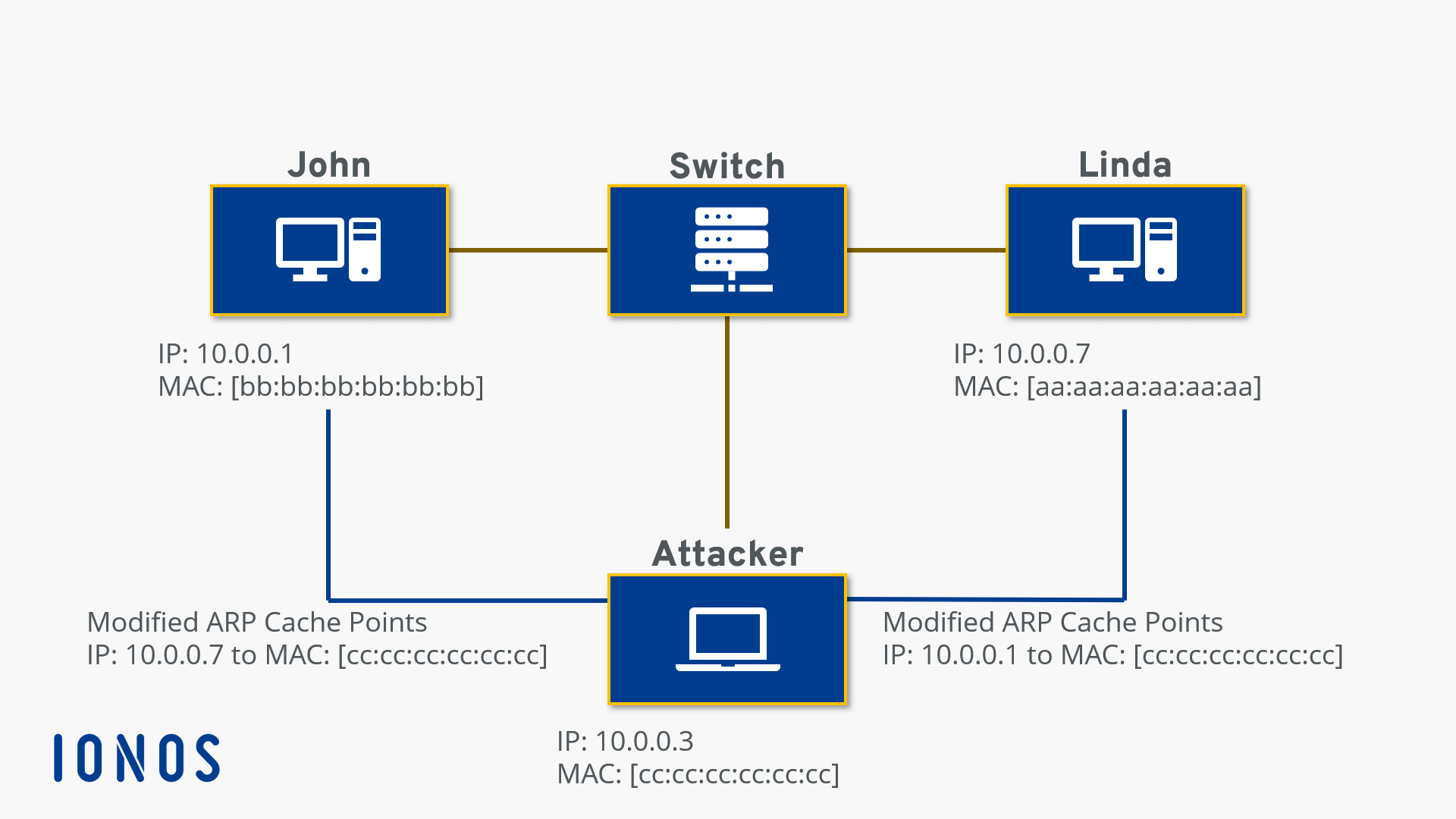
| Uploader: | JoJobei |
| Date Added: | 6 December 2015 |
| File Size: | 64.74 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 66880 |
| Price: | Free* [*Free Regsitration Required] |
An introduction to Network Security.
This article needs additional citations for verification. In the previous tutorial, you saw how you can write a MacChanger using Python.
Unsourced material may be challenged and removed. Spofer, the goal of the attack is to associate the attacker's host MAC address with the IP address of a target hostso that any traffic meant for the target host will be sent to the attacker's host. How Application Security Works? Get personalised resources in your inbox. There is no method in the ARP protocol by which a host can authenticate the peer from which the packet originated.
Hosts don't need to transmit ARP requests where such entries exist. Already have an account?
Well, that will be the router spooter the Virtual Machines are connected to. Ethical Hacking and Python. Please help improve this article by adding citations to reliable sources.
For this tutorial, I am using Virtual Machines to create nodes. The latter has recently run into significant problems with its ARP-spoofing strategy in consumer's homes; they have now completely removed that capability and replaced it with a DHCP -based strategy. How To Install Kali Linux? Linux ignores unsolicited replies, but, on the other hand, uses responses to requests from other machines to update its cache. What is Ethical Hacking?
For example, some software allows a backup server to issue a gratuitous ARP request in order to take over for a defective server and transparently offer redundancy.
ARP Spoofing – Automating Ethical Hacking with Python
Do you know how the data flows when you are connected to the router? ArpStar is a Linux module for kernel 2.
But for this demo, we will make it easy. The router sends data to the IP address of your system and your system sends data to the IP address of the router.
Introduction to Computer Security Read Article. Uncertified ARP responses are then blocked. The simplest form of certification is the use of static, read-only entries for critical services in the ARP cache of a host. Please enter a valid emailid. It is common that everyone uses WiFi these days and you are one of them.
bettercap ::
Retrieved from " https: How to choose the Best? Interested in anything and everything about Computers. This training will help you understand Cybersecurity in depth and help you achieve mastery over the subject. This capability may be implemented in individual hosts or may be integrated into Ethernet switches or other network equipment. You will now see the workplace. Look at the MAC address of the router, this will change after we run the script.
The attacker may choose to inspect the packets spyingwhile forwarding the traffic to the actual default destination to avoid discovery, modify the data before forwarding it man-in-the-middle attackor launch a denial-of-service attack by causing some or all of the packets on the network to be dropped.
This packet is known as an ARP request.

Комментариев нет:
Отправить комментарий